Implement Security Testing in your SDLC
What is SDLC and its phases?
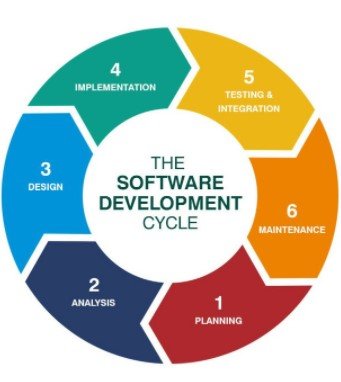
SDLC, or Software Development Life Cycle, is a framework for improving the quality and reliability of software that's been built. It uses a variety of models to accomplish this, but they all share some similar objectives. Let's talk about the different phases of SDLC.
The SDLC life cycle begins with the planning and requirement analysis phase. We typically contact the client to acquire all relevant information, such as the functionality they require in the product and their specific requirements. After obtaining all of the requirements, the team analyzes how they will develop the software, such as connecting with hardware, databases and what technologies will be required, among other things.
After SRS, the team moves on to the design phase, constructing a rough design for the customer. The plan contains the user interface (UI) and the features that are being implemented, so the client can get a sense of what features are being developed and how they are being implemented and recommend adjustments if necessary.
After the design phase, the team starts implementing the design in the proper software, they use programming languages to implement the feature and the logic required to create the working software.
After the building phase, testing is carried out. It is critical to test all developed features as there may be some flaws with the logic or functionality. There may be a security vulnerability in the software that could pose a threat to the organization. So, before deploying the main product, it's essential to patch those flaws. They can be identified by source code review, automated tools, or manual penetration testing. Once the product has been thoroughly tested, the software is ready to be deployed on the client's site.
But sometimes, source code analysis is challenging. Developers want to automate this process so that they can pin down the vulnerabilities easily. A standard solution is IAST, which combines DAST and SAST; its testing occurs in real-time and can also be integrated with the CI/CD pipeline. It works by deploying the agents and sensors in the application's post-build. After product deployment, the team monitors it for some time to patch any new vulnerabilities that may occur in the meantime. This is the maintenance phase.
What is security and application testing?
Security provides defense and protects our infrastructure from internal and external threats. Detection, prevention, and mitigation are all included in the phrase defense.
Every organization has a defense policy. During application testing, the tester examines vulnerabilities that could pose a risk to the organization. They look for any potential flaws that an attacker could use to abuse their reputation, revenue, secret information, or non-compliance. They are some of the primary factors that a pen-tester considers when testing an application.
Confidentiality is the first aspect to be checked, which implies that securing Personally Identifiable Information (PII) is the most basic security criterion that the organization must meet.
In the case of integrity testing, the goal is to uncover any vulnerabilities that give an attacker unauthorized access to the application, allowing him to change the user's data or other information. In this instance, the software's integrity is jeopardized. Suppose the attacker wants to hide his traces. In that case, he primarily uses the non-repudiation technique. He deletes all the unauthorized access logs to conceal his identity and remove traces of any attacks.
If the attacker cannot get any unauthorized access to the application, he tries to make the application unavailable for other users by doing the DOS (Denial of Service) on the application's server.
Implementing Security Testing in SDLC
Each phase of the SDLC gives security testing a high priority, and security is handled differently in each stage.
Phase 1: Requirements
We must identify security aspects based on data, such as checking if data encryption is implemented or not, as all information is acquired, how the data flow will look, and how it is being sent from the user to the server. We derive from the requirement phase whether the application has any PII Data or deals with any payment details.
Phase 2: Design
As we have an authentic look and feel of the application in this phase, security professionals perform threat modeling and design review. Based on threat modeling, they try to identify what threats may occur in the application and what countermeasures should be taken to mitigate them. So it gives developers a clear picture of where they need to enable the security controls. let take some example
During threat modeling, we look closely at the factors that could lead to a vulnerability, such as how user inputs are handled, sanitized before being reflected on the web page, or transferred to SQL queries. Without input validation, vulnerabilities like XSS and SQL injection could occur.
Phase 3: Development
Software is implemented in this phase using a programming language. Still, security professionals have to check whether code is written as per the security standards, such as input validation is being performed or not. White-box testing or static analysis is done in this phase. We have secure coding requirements in every organization that one must follow to the letter. During this phase, one checks if standards are being followed correctly, such as how input validation is done and how the application handles user data.
Phase 4: Testing
In this phase, one will recheck security assessment and configuration to ensure that the application meets the original design and requirements. Here automated tools and software security testing comes into existence. The application does not deploy till these test cases are not passed. The application has been fully developed and ready to use; application owners employ automated tools in conjunction with a manual penetration tester to seek vulnerabilities in the software. Application owners also use the CI/CD Process to automate testing with IAST.
Phase 5: Maintenance and Evolution
Now, the application has been deployed. However, security professionals begin conducting vulnerability management in this phase to manage dependencies that may lead to potential vulnerabilities. Hence, it is indispensable to have a vulnerability management program to keep track of them. Some companies like Facebook and Google start their bug bounty program and invite independent researchers to test their resources to uncover some vulnerabilities.
Conclusion
SDLC provides a systematic approach to build and deploy an application with minimum vulnerabilities. But there is also a need to implement security so that the application can function correctly. Every phase of SDLC includes different security aspects, and if they are followed, then there is a possibility that you can build a great product.