
VeraCrypt
In a atmosphere of more and more cryptocurrency hacks and theft, I would urge all serious cryptocurrency traders or investors to take the necessary security measures. Private keys, seeds , two factor keys etc needs to be protected at all costs, after all, your private keys/seeds is your money!
Here i will try to make a very easy description on how to set up your veracrypt file container :
Step 1
Download Veracrypt
Step 2
When installed, open veracrypt. You should see this screen :
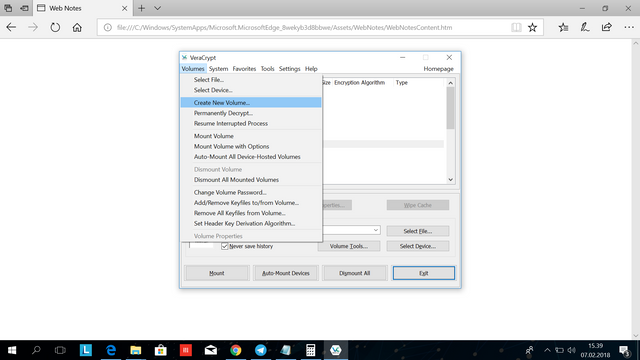 Click Create New Volume
Click Create New Volume
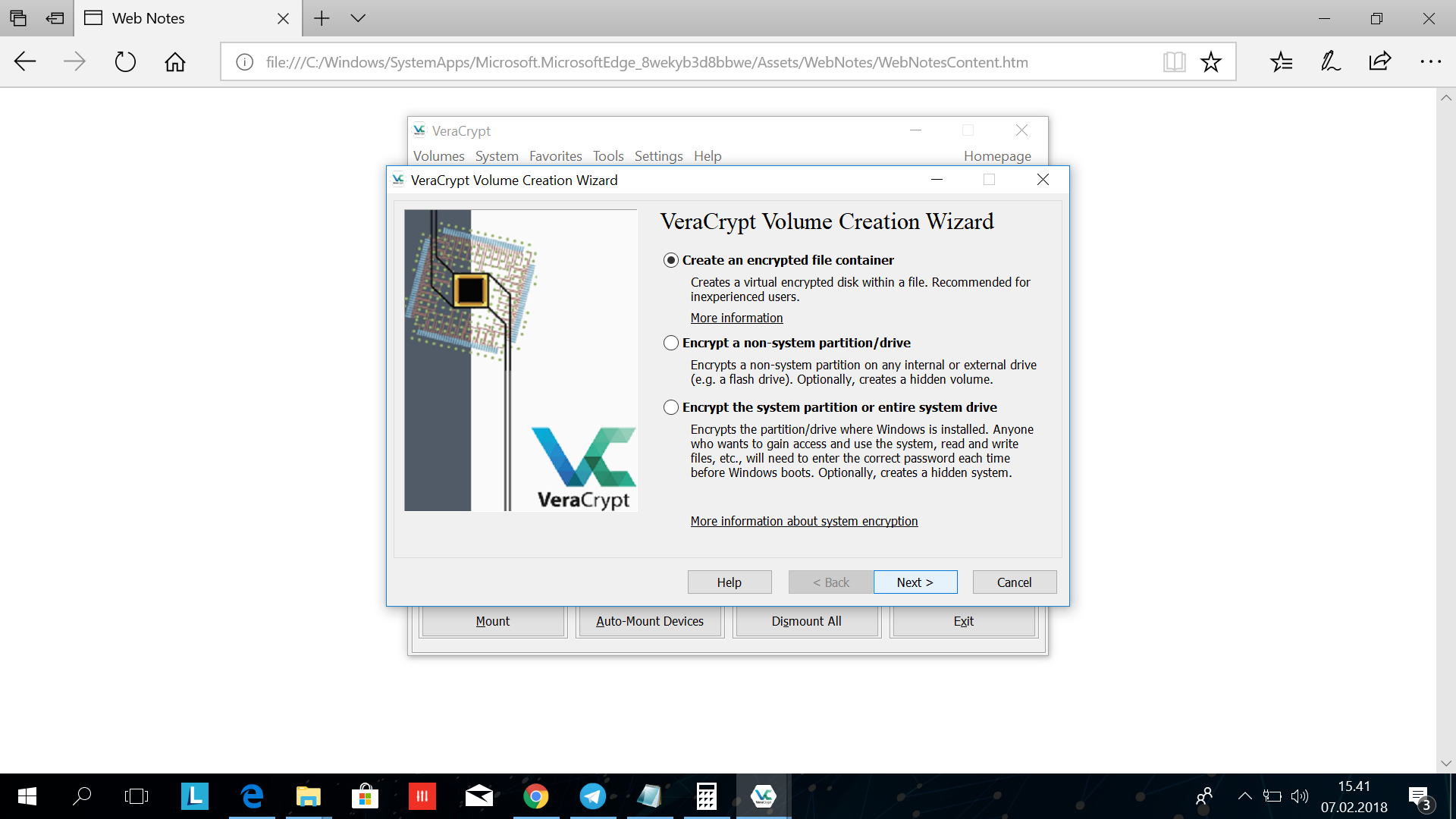 Check the "create an encrypted file container" and click next
Check the "create an encrypted file container" and click next
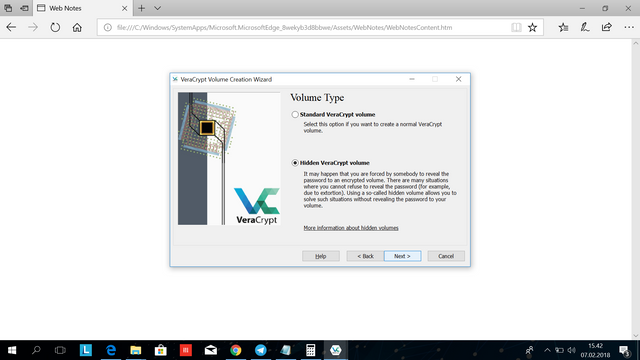 Check the box "Hidden VeraCrypt volume" and click next
Check the box "Hidden VeraCrypt volume" and click next
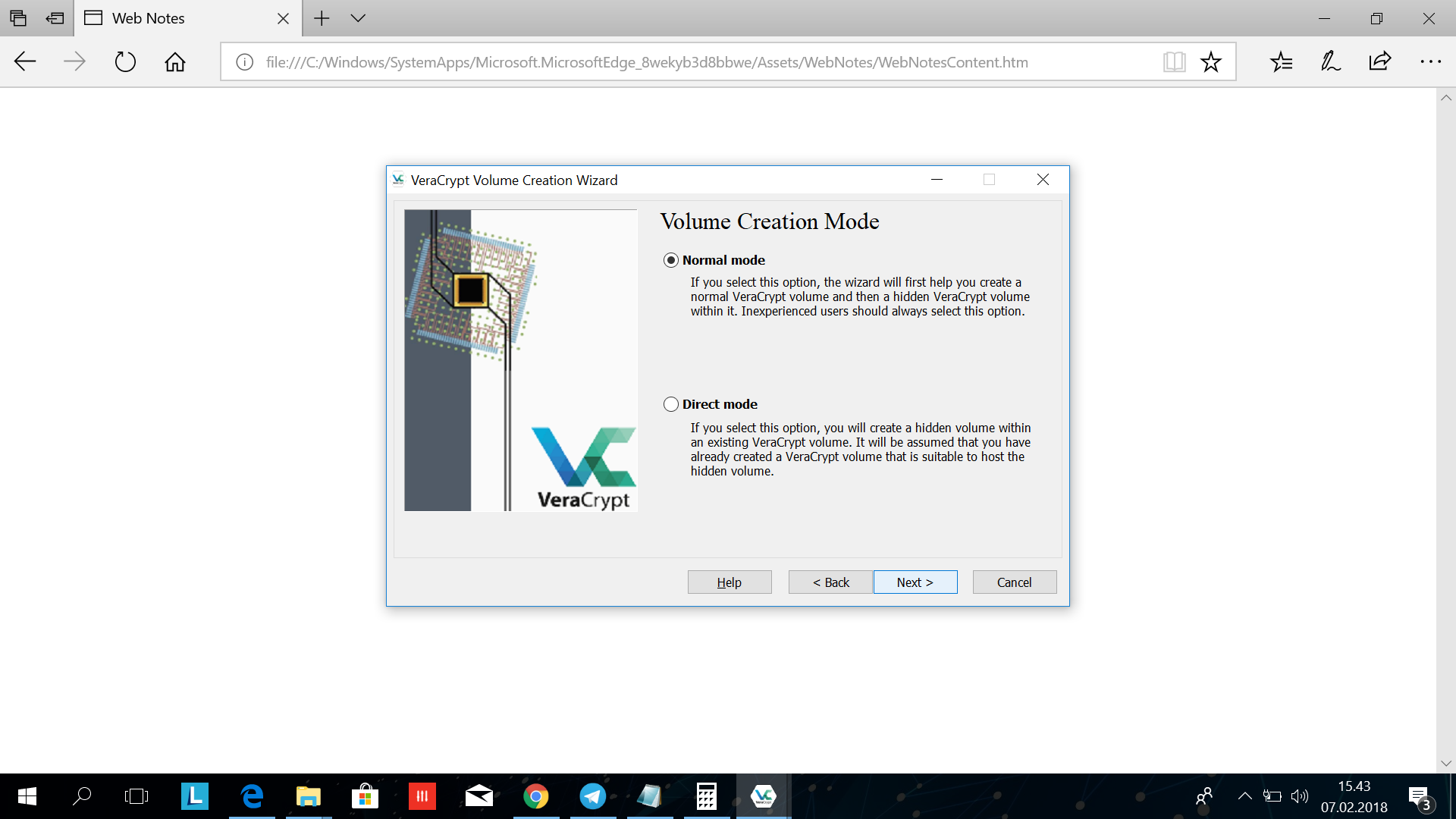 Choose "Normal Mode" and click next
Choose "Normal Mode" and click next
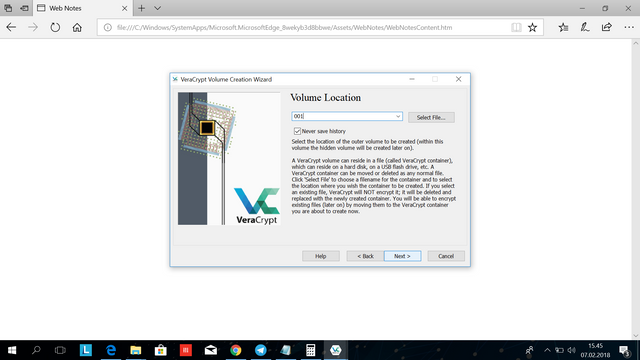 Here you get asked for the volume location. Since the volume does not exist, here you enter the name of your volume and click next. (The volume will be saved in your /user directory by default.
Here you get asked for the volume location. Since the volume does not exist, here you enter the name of your volume and click next. (The volume will be saved in your /user directory by default.
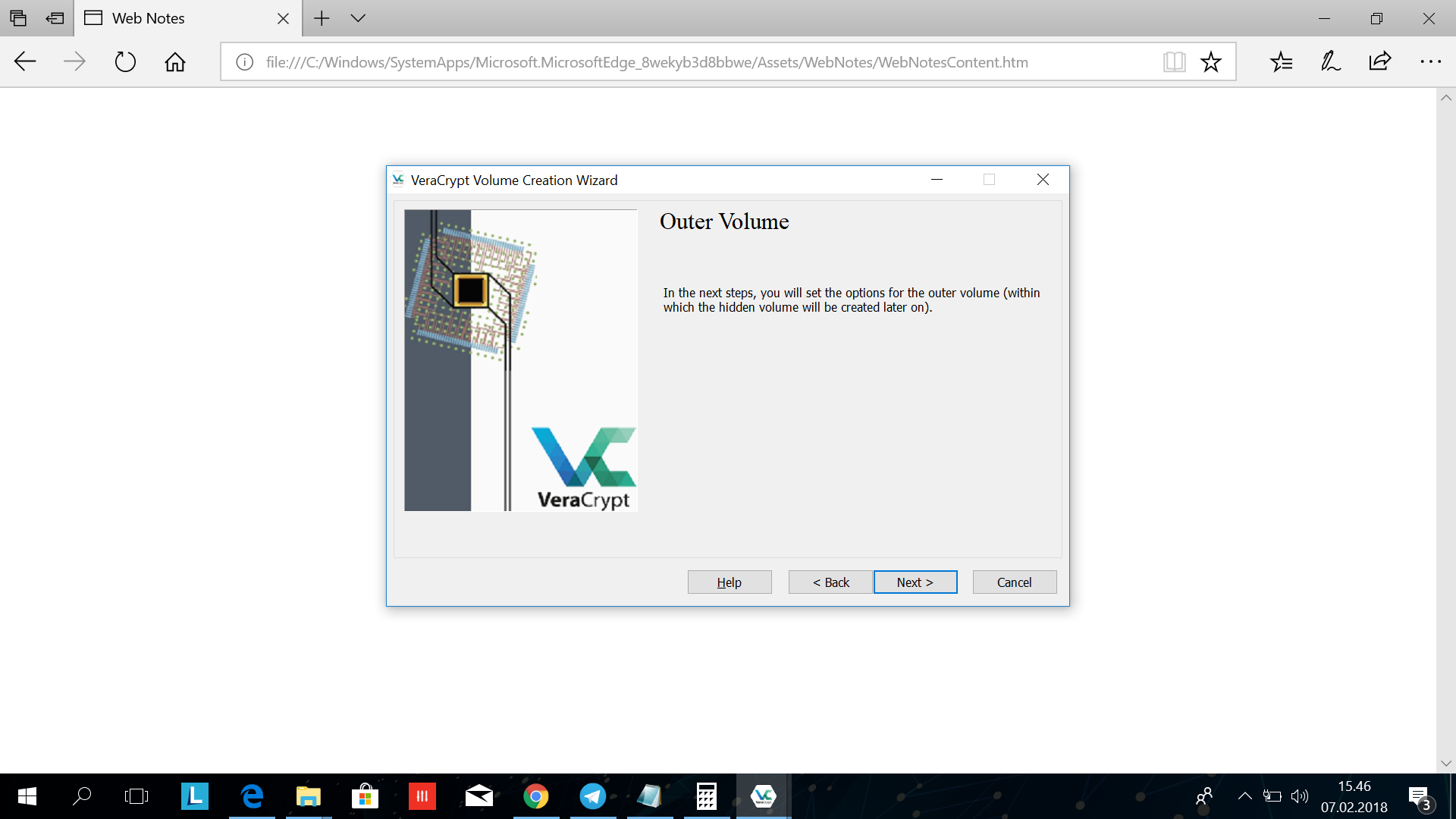 Now you will set the options for the outer volume. This is the volume which you will give up to in case of extortion. Basicly this is a fake volume that should be filled with fake sensitive files. Click Next.
Now you will set the options for the outer volume. This is the volume which you will give up to in case of extortion. Basicly this is a fake volume that should be filled with fake sensitive files. Click Next.
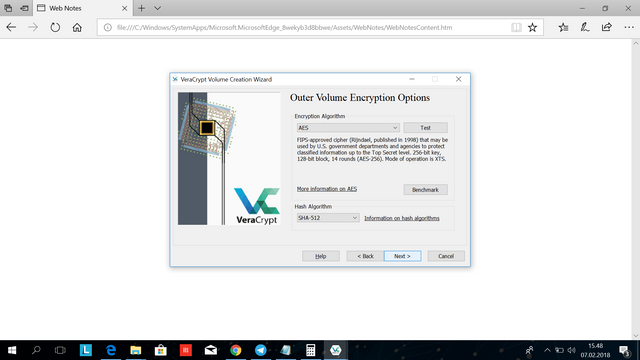 Dont do anything here, click next.
Dont do anything here, click next.
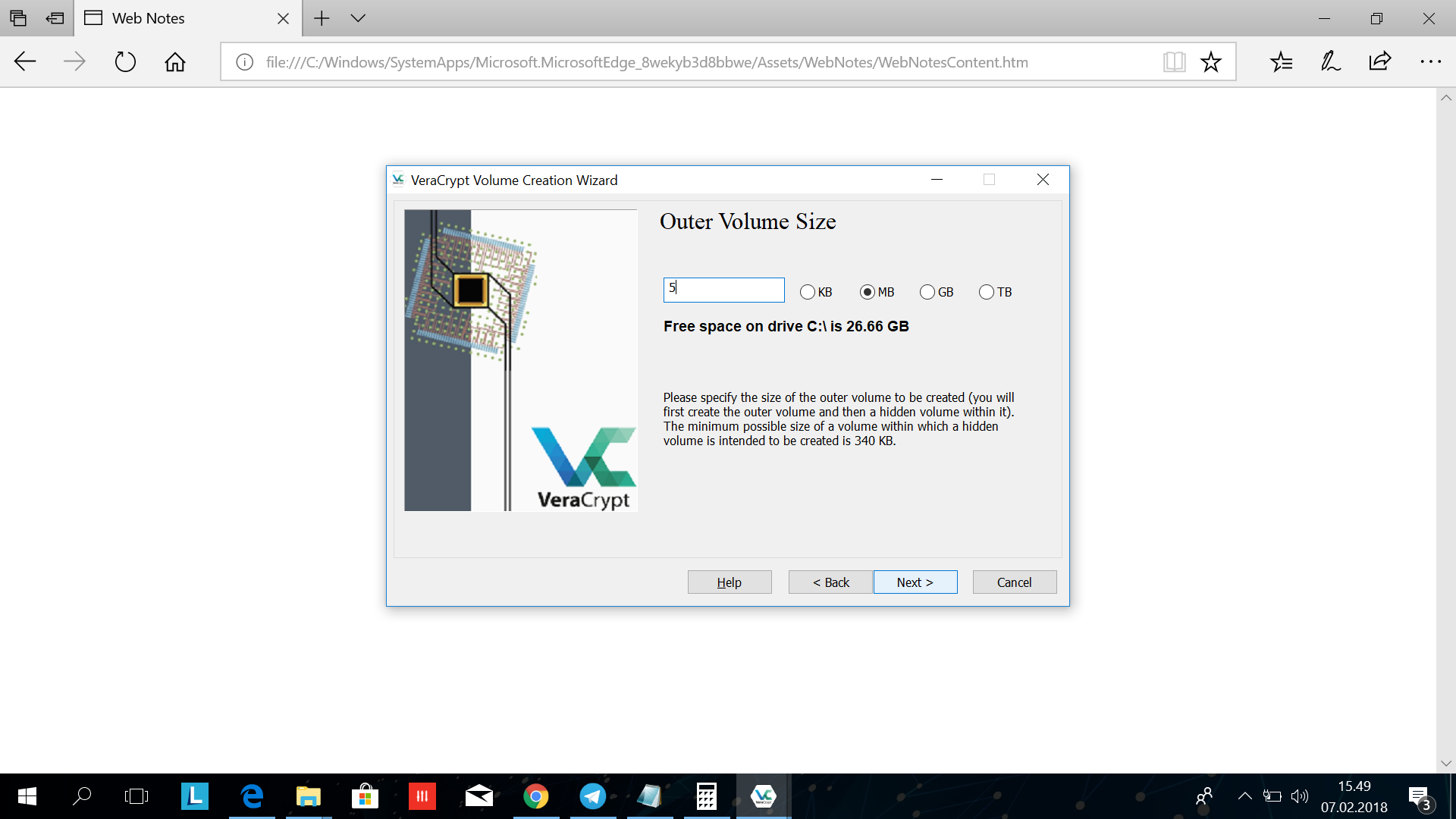 Here you choose the volume size for the outer volume. This does not need to be bigger than the files ment to be in that container. In our cases this is mostly textfiles, so 5 mb should be more than enough.
Here you choose the volume size for the outer volume. This does not need to be bigger than the files ment to be in that container. In our cases this is mostly textfiles, so 5 mb should be more than enough.
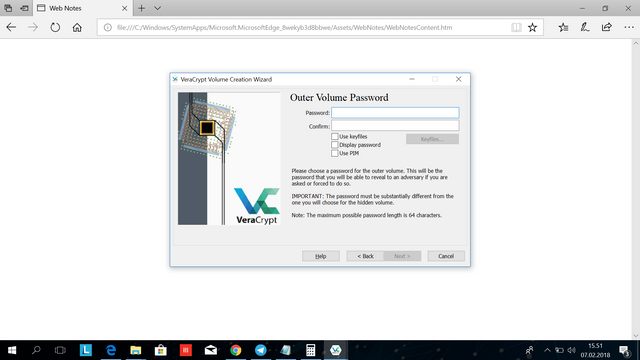 Here you will enter the password for the outer (fake) volume, this password have to be totally different from the password you use when making the hidden volume. When done, click next
Here you will enter the password for the outer (fake) volume, this password have to be totally different from the password you use when making the hidden volume. When done, click next
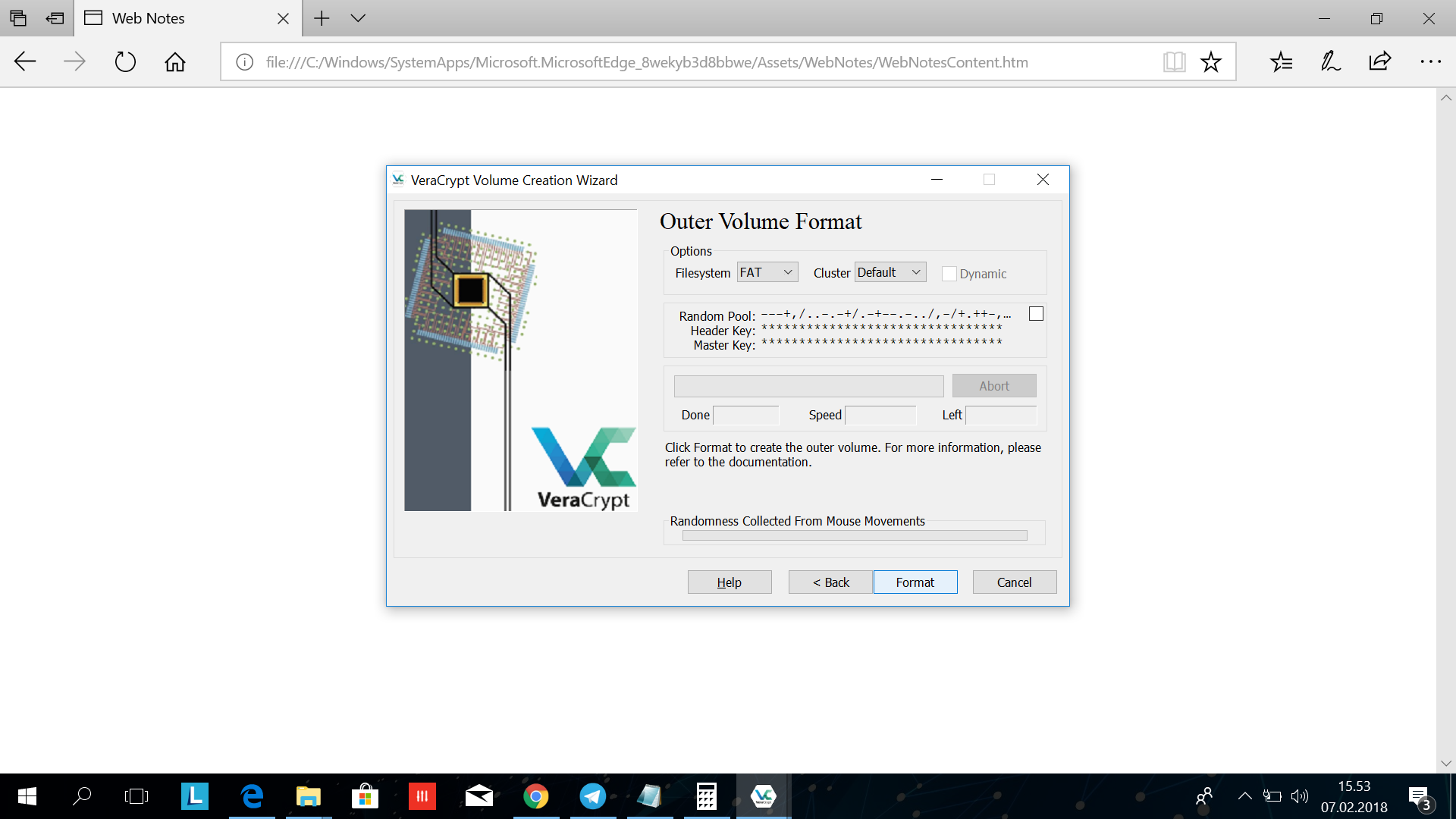 When you come to this screen, move your cursor over the VeraCrypt windows until the bar in the bottom turns full green
When you come to this screen, move your cursor over the VeraCrypt windows until the bar in the bottom turns full green
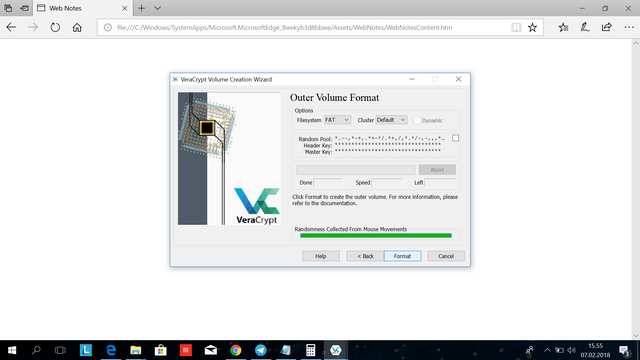 When you have moved your cursor around inside the windows quite a bit, it should eventually get full..
When you have moved your cursor around inside the windows quite a bit, it should eventually get full..
Now you have created enough randomness to format the outer volume. Click format.
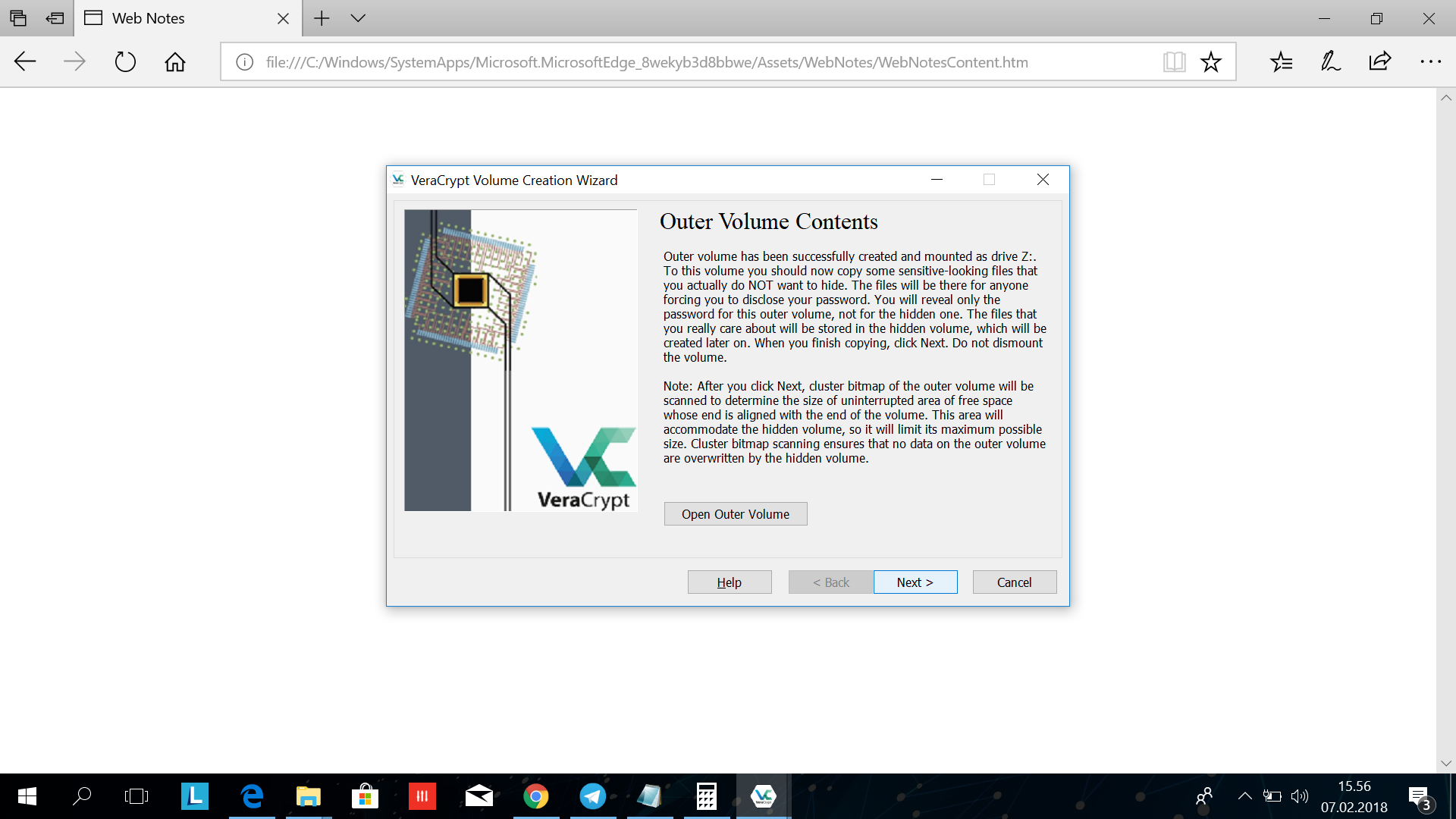 After formatting, choose "open outer volume" and place the "fake" seeds and sensitive files in this folder. Click next when you have copied your files.
After formatting, choose "open outer volume" and place the "fake" seeds and sensitive files in this folder. Click next when you have copied your files.
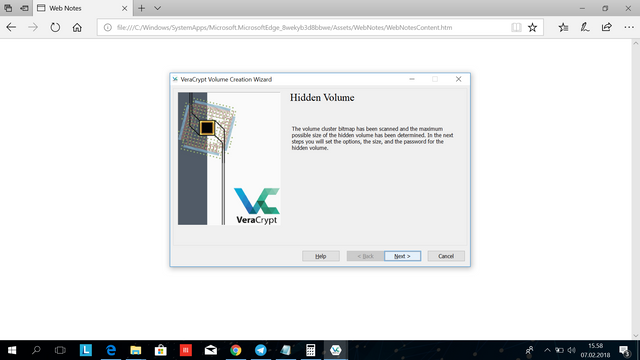 You will now be shown this window, you will now determine the specifics of your hidden volume, click next.
You will now be shown this window, you will now determine the specifics of your hidden volume, click next.
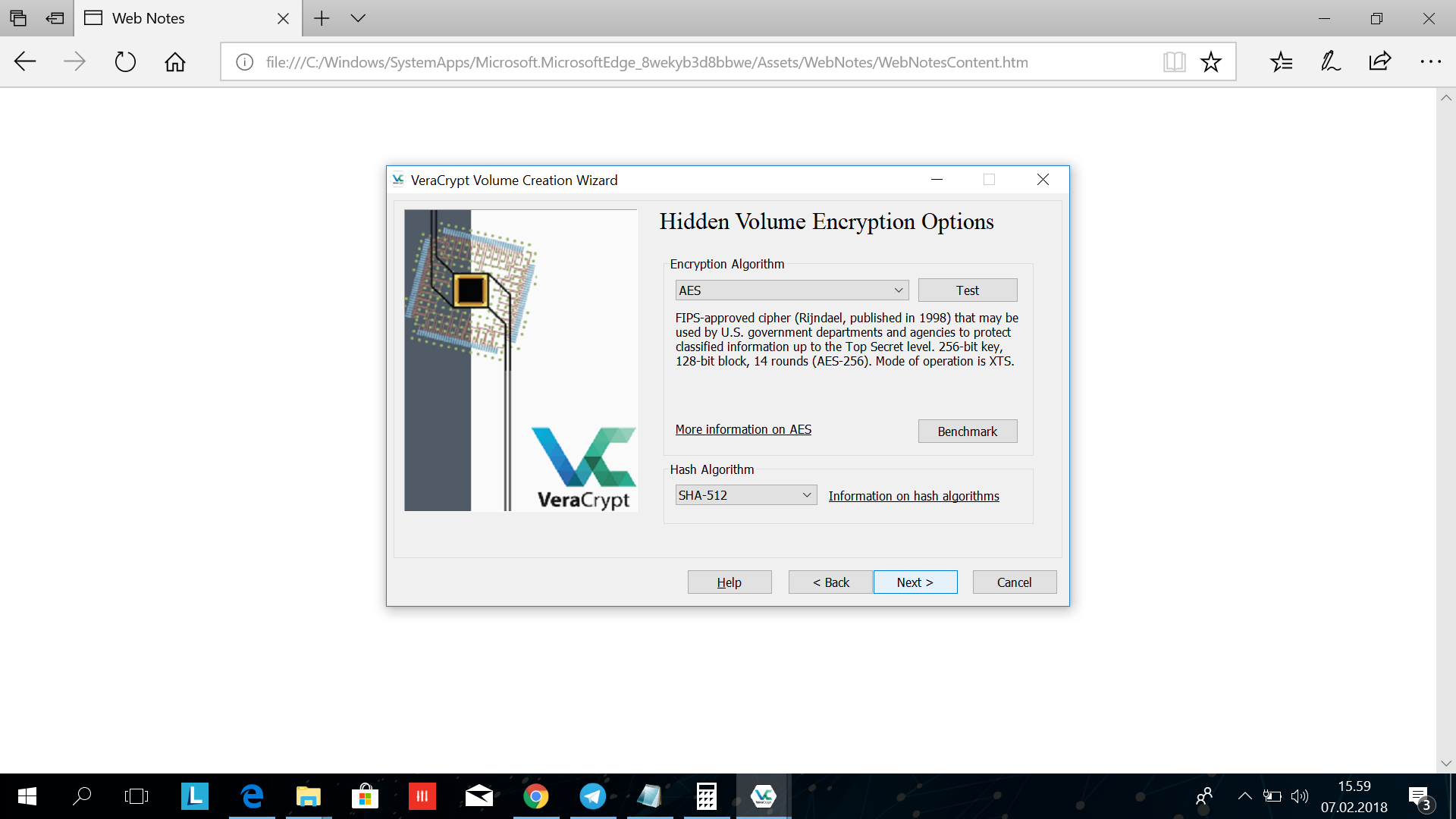 Click next.
Click next.
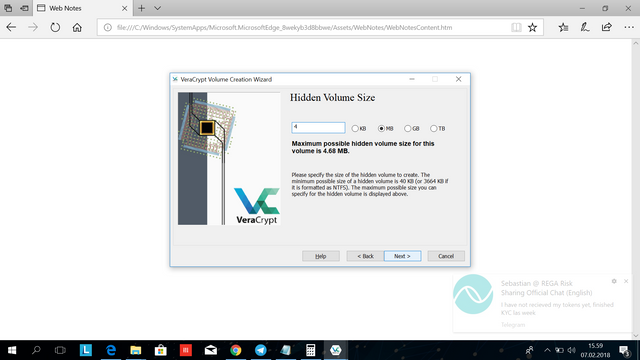 Here you choose the size of the hidden volume, click next.
Here you choose the size of the hidden volume, click next.
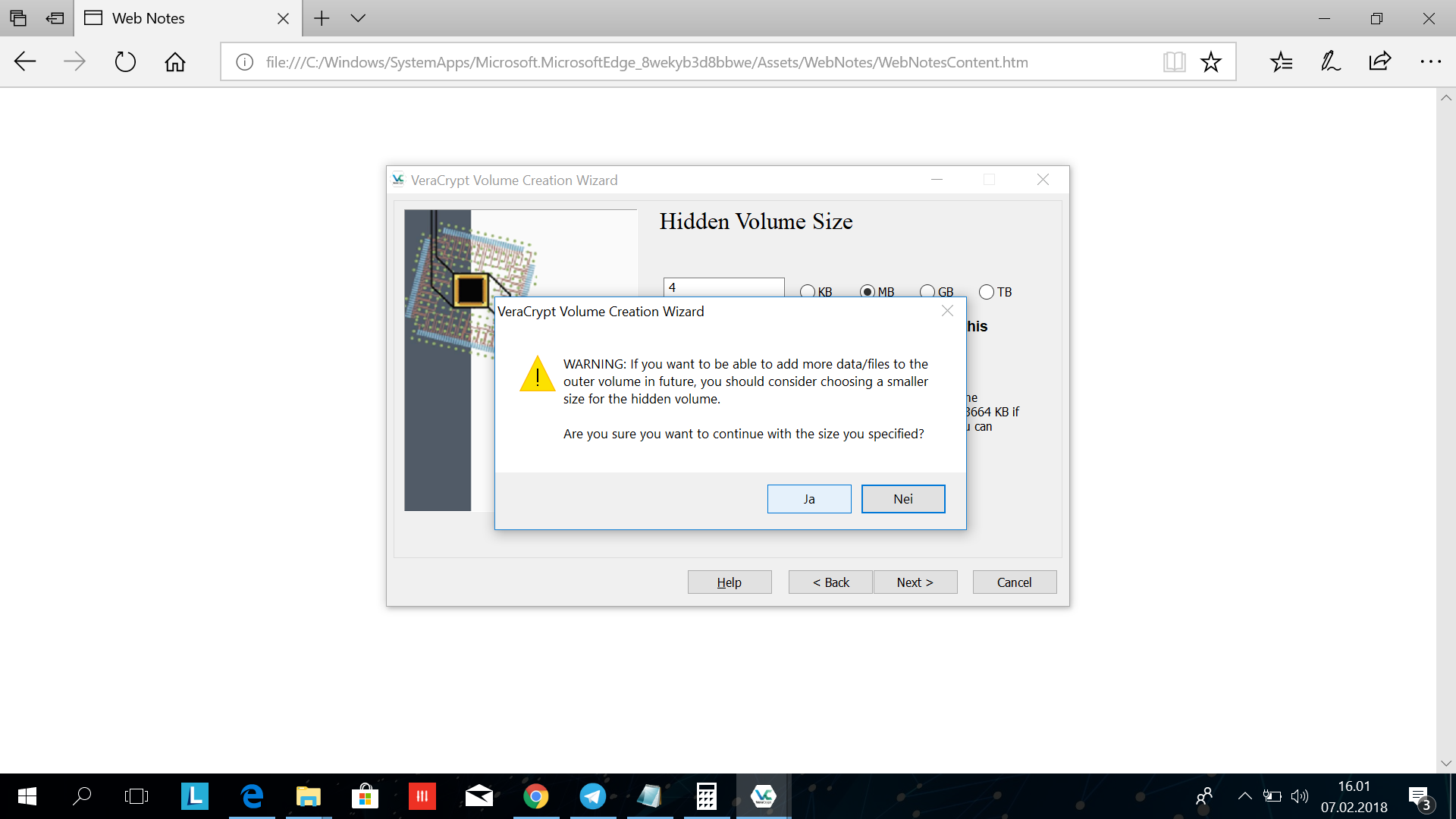 In this windows you get prompted that you should not keep adding new files to the other volume because of the way it is structured, click Yes.
In this windows you get prompted that you should not keep adding new files to the other volume because of the way it is structured, click Yes.
 The next step is to choose the password for the hidden volume. This password should be as long as possible (64 char). Click next.
The next step is to choose the password for the hidden volume. This password should be as long as possible (64 char). Click next.
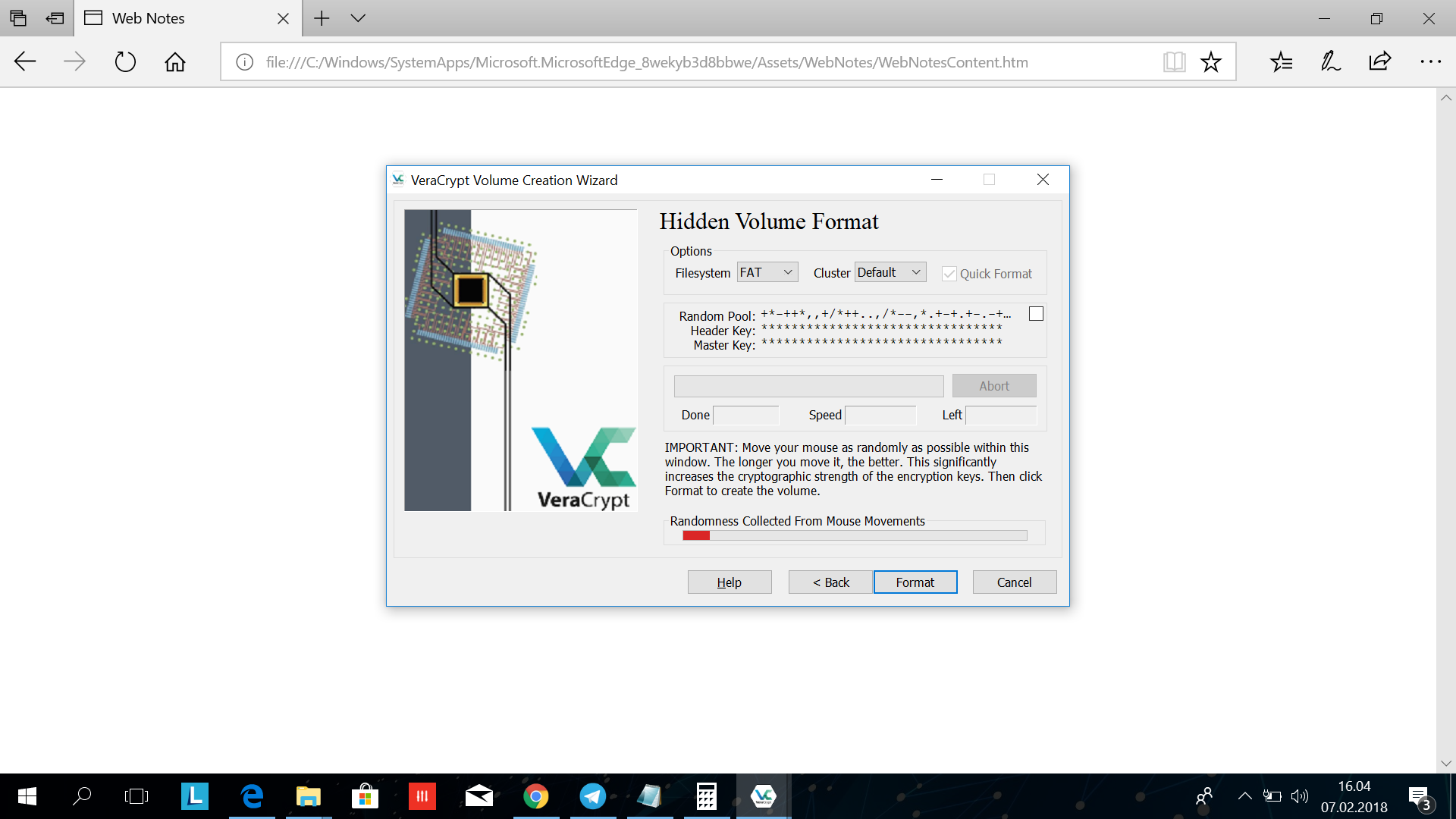 Here is the same deal all over again. Move your mouse cursor over the veracrypt windows until veracrypt has collected enough randomness, then click "format".
Here is the same deal all over again. Move your mouse cursor over the veracrypt windows until veracrypt has collected enough randomness, then click "format".
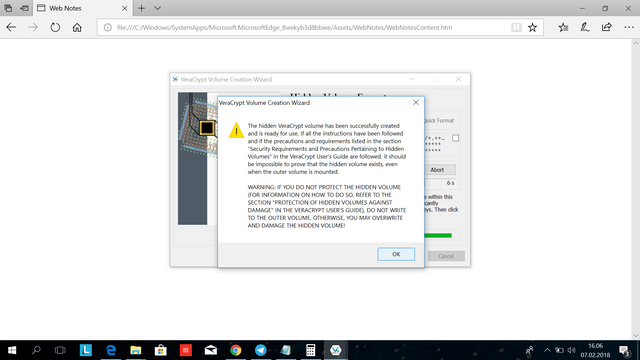 Click ok.
Click ok.
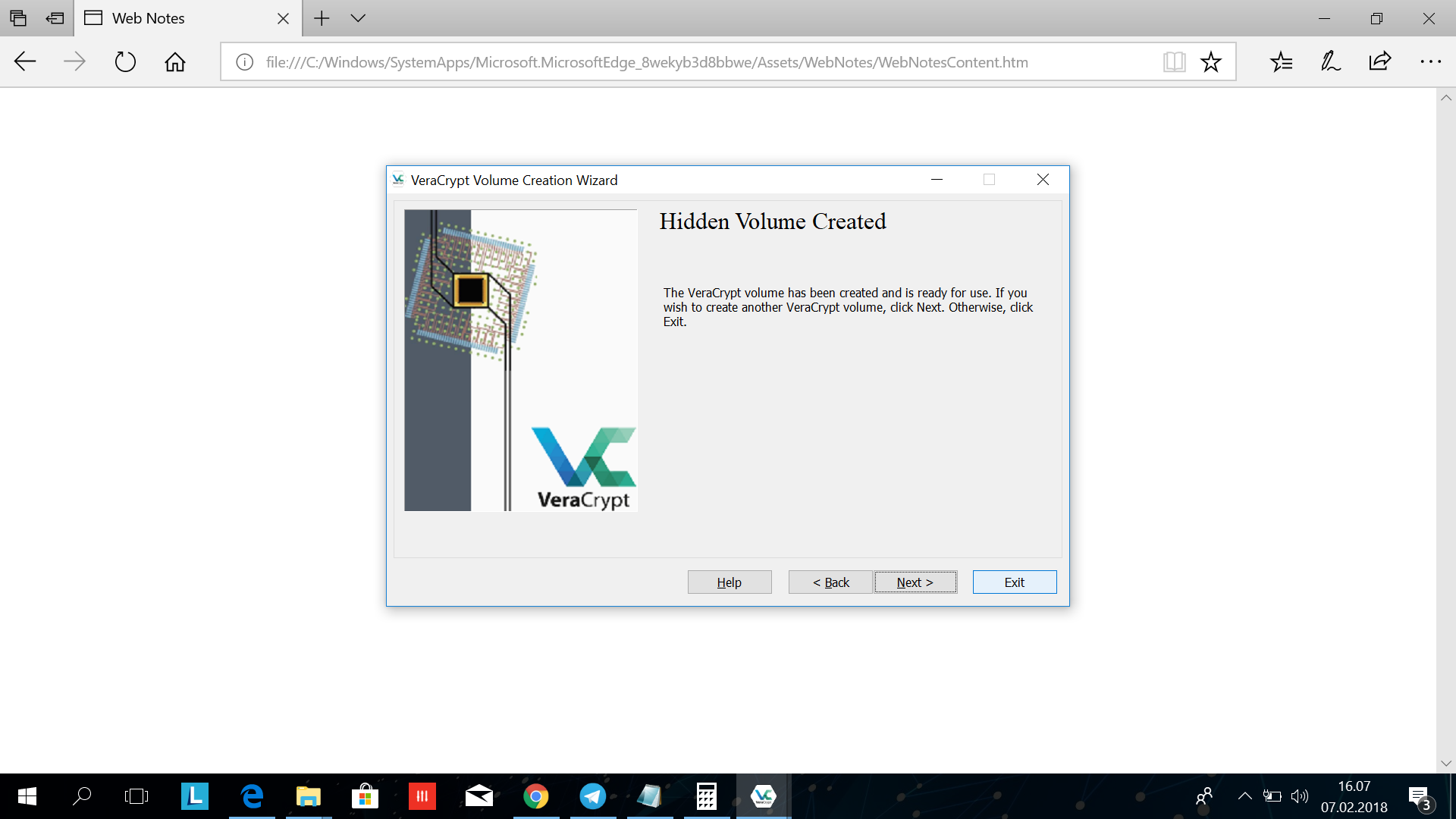 You have now successfully made your veracrypt volume. Click quit.
You have now successfully made your veracrypt volume. Click quit.
How do open my VeraCrypt volumes ?
Open VeraCrypt
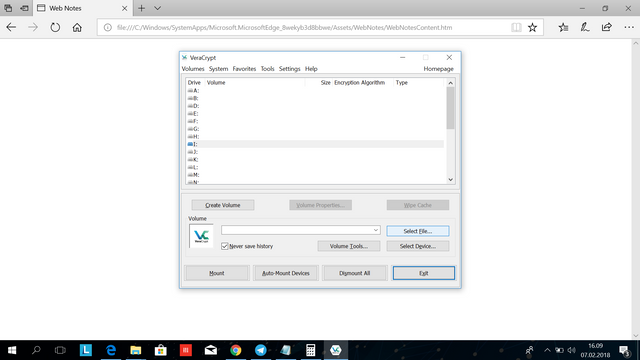 Choose select file. Choose the newly created volume and open.
Choose select file. Choose the newly created volume and open.
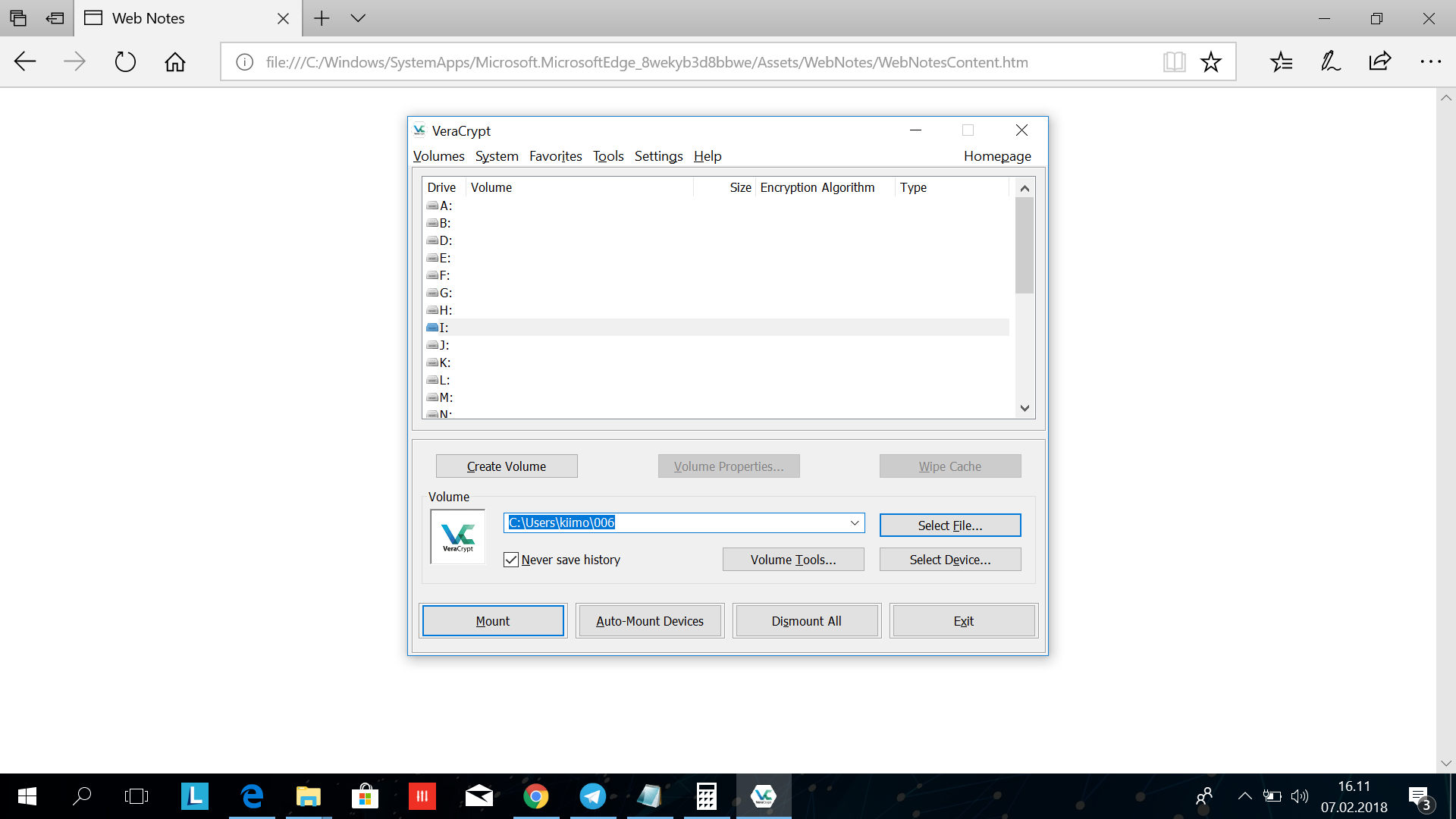 Now the window look like this. Notice your volume is selected down in the volume area.
Now the window look like this. Notice your volume is selected down in the volume area.
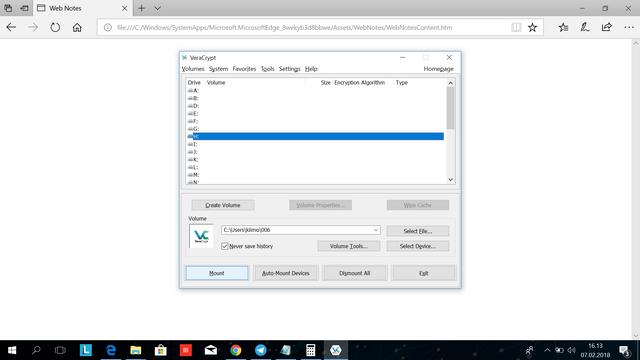 Choose a vacant drive and click mount.
Choose a vacant drive and click mount.
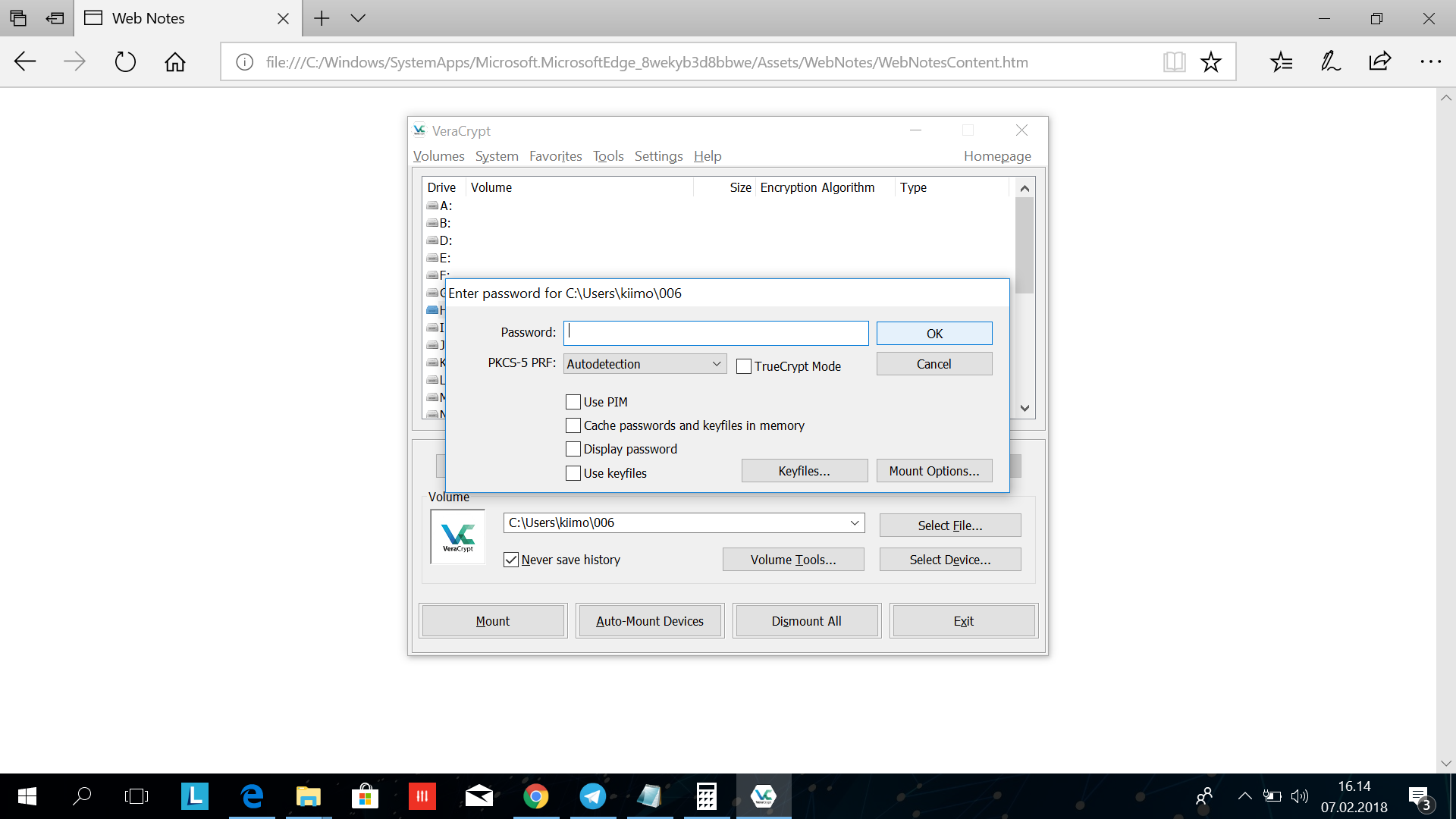 You will now be asked for the encryption password. In this case you can enter both the outer volume password (which of course leads you to the "fake" outer volume) and the hidden volume password. In the case of extortion you would want to access your outer volume only. In the case where you need access to your sensitive information you enter the "hidden volume" password (I would generally only open my volumes at a dedicated machine which have never been used for internet surfing)
You will now be asked for the encryption password. In this case you can enter both the outer volume password (which of course leads you to the "fake" outer volume) and the hidden volume password. In the case of extortion you would want to access your outer volume only. In the case where you need access to your sensitive information you enter the "hidden volume" password (I would generally only open my volumes at a dedicated machine which have never been used for internet surfing)
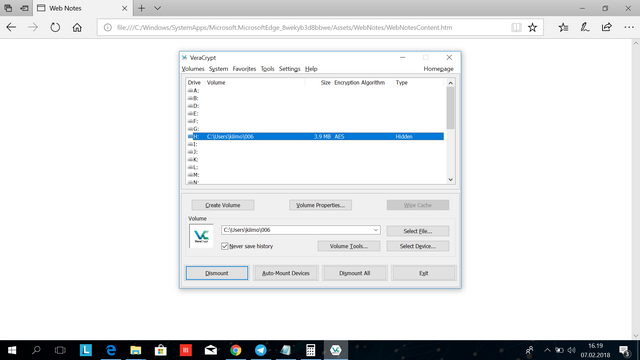 You have now successfully mounted the hidden volume (if you entered the password for the hidden volume) and it will appear under the drive you chose. Double click the volume and the folder will appear. Drag all your sensitive files into this folder, close it, return to VeraCrypt and click unmount.
You have now successfully mounted the hidden volume (if you entered the password for the hidden volume) and it will appear under the drive you chose. Double click the volume and the folder will appear. Drag all your sensitive files into this folder, close it, return to VeraCrypt and click unmount.
 After you unmount, mount it again and check that both the outher volume password and inner volume passwords are correct and that the volume isnt damaged in any way before you delete your sensitive files. You can now store your sensitive information safely. But i would recommend to only open volumes on a offline computer not connected to the internet for maximum security!
After you unmount, mount it again and check that both the outher volume password and inner volume passwords are correct and that the volume isnt damaged in any way before you delete your sensitive files. You can now store your sensitive information safely. But i would recommend to only open volumes on a offline computer not connected to the internet for maximum security!
Be safe!



























i will try this
This post has received a 0.69 % upvote from @booster thanks to: @hamlander.